MEV 回调函数漏洞分析
- Archime
- 发布于 2022-12-12 20:14
- 阅读 4725
MEV 回调函数漏洞分析
1. 漏洞简介
Another interesting attack for @AnnexFinance. 5 of their liquidator contracts have been attacked. The lost is a small amount($3000) but the vulnerability is interesting.
There are total 5 attack TX related to these on BSC. One example is https://bscscan.com/tx/0x3757d177482171dcfad7066c5e88d6f0f0fe74b28f32e41dd77137cad859c777, attacker 0x40fB8d322cC4887D6c2Bf886755300EA79f6A874 gained around 0.2 ETH which is about $2,000.
The root cause is that the contract does not verify caller and pass in parameters in pancakeCall() functions. It could let attacker transfer the estuary tokens to attacker controlled panswap contract.
2. 相关地址或交易
https://bscscan.com/address/0xe65e970f065643ba80e5822edff483a1d75263e3#code Liquidator 合约 https://bscscan.com/tx/0x3757d177482171dcfad7066c5e88d6f0f0fe74b28f32e41dd77137cad859c777 攻击交易
3. 获利分析
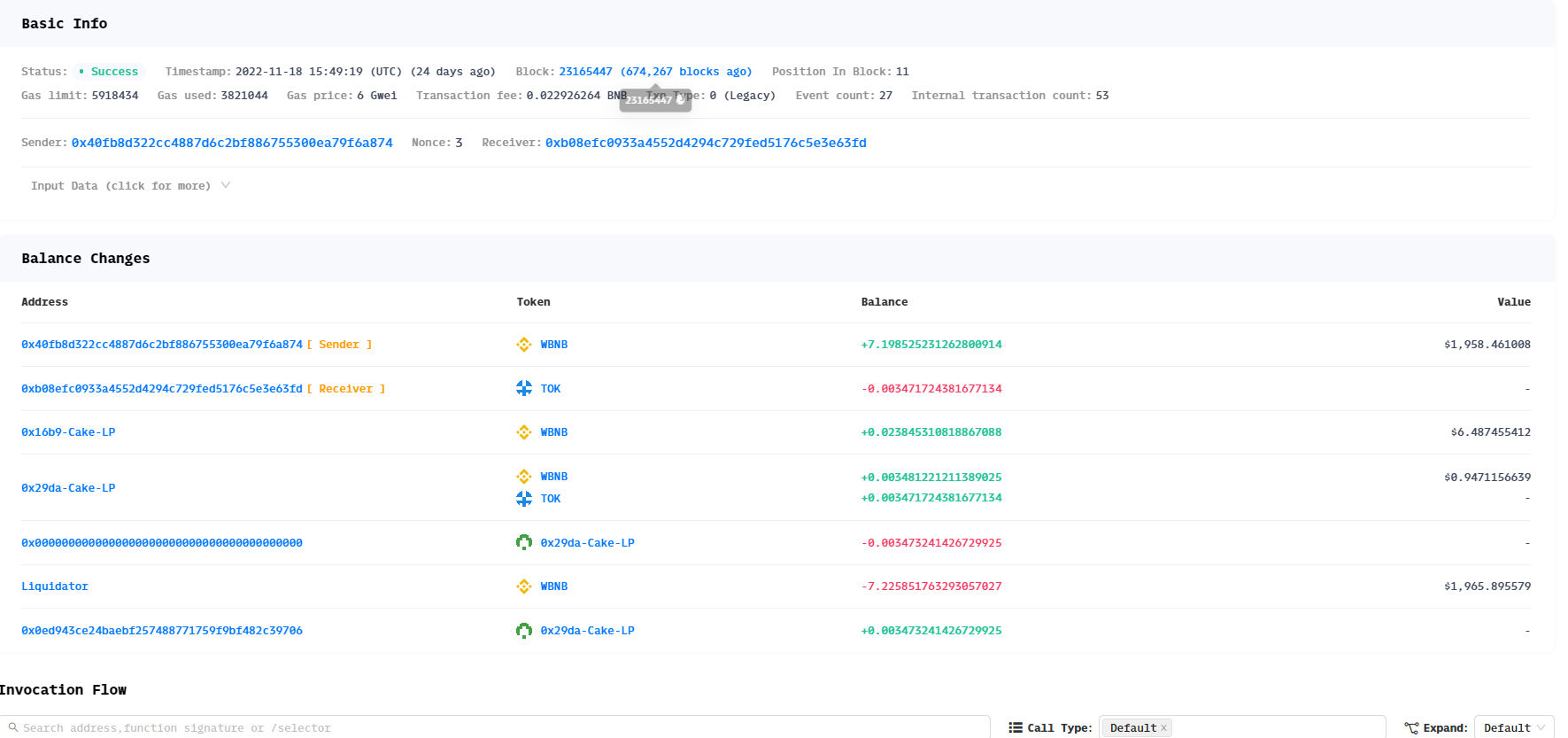
4. 攻击过程&漏洞原因
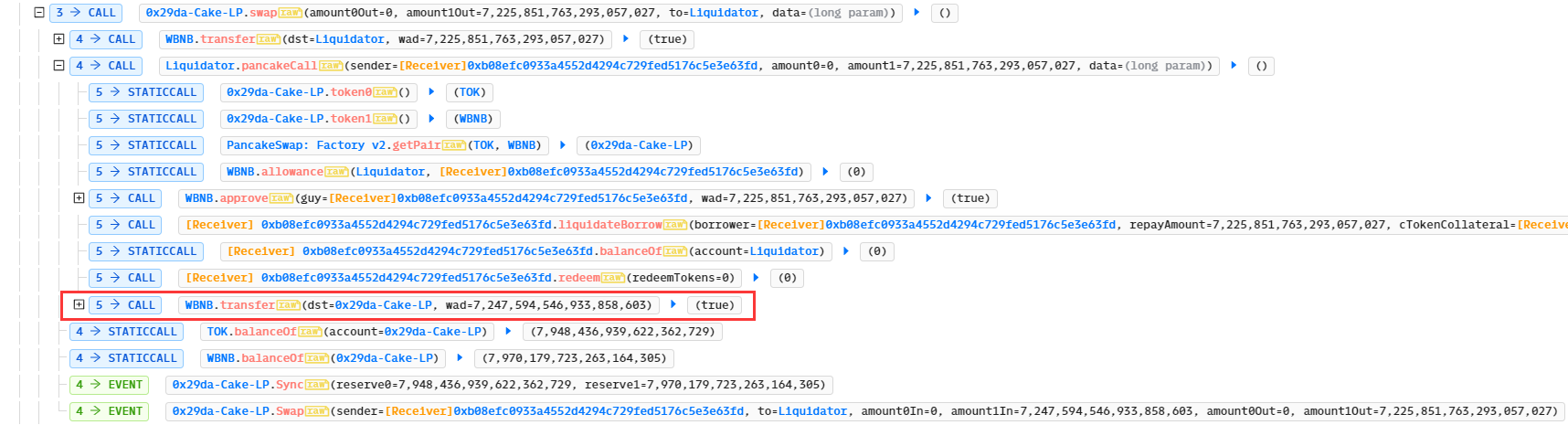
在Liquidator合约中存在回调函数pancakeCall,其中存在判断条件require(msg.sender == IPancakeFactory(FACTORY).getPair(token0, token1)); 即调用方必须为工厂合约IPancakeFactory(FACTORY)返回的交易对的池子地址。 利用步骤
- 可先创建垃圾代币后再通过工厂合约PancakeFactory创建新的交易对,从而绕过漏洞合约的检查。
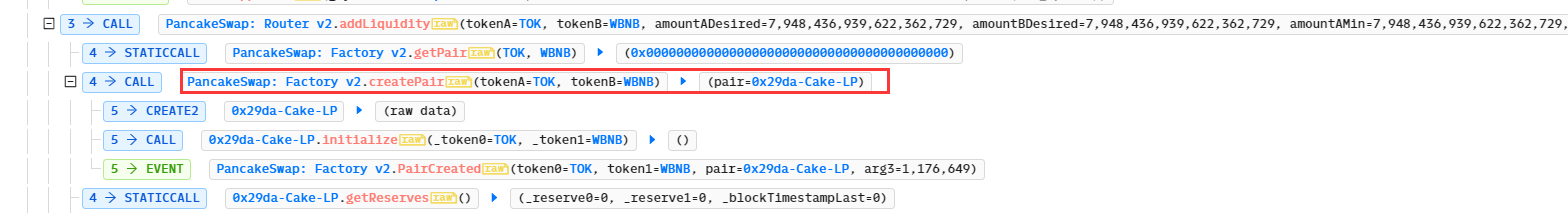
- 再调用刚创建的合约0x29da-Cake-LP的闪电贷swap()方法,此时指定接收者为漏洞合约Liquidator,data为利用逻辑。因为此时IPancakeFactory(FACTORY).getPair(token0, token1) 返回的值为0x29da-Cake-LP,即可绕过Liquidator的检查:
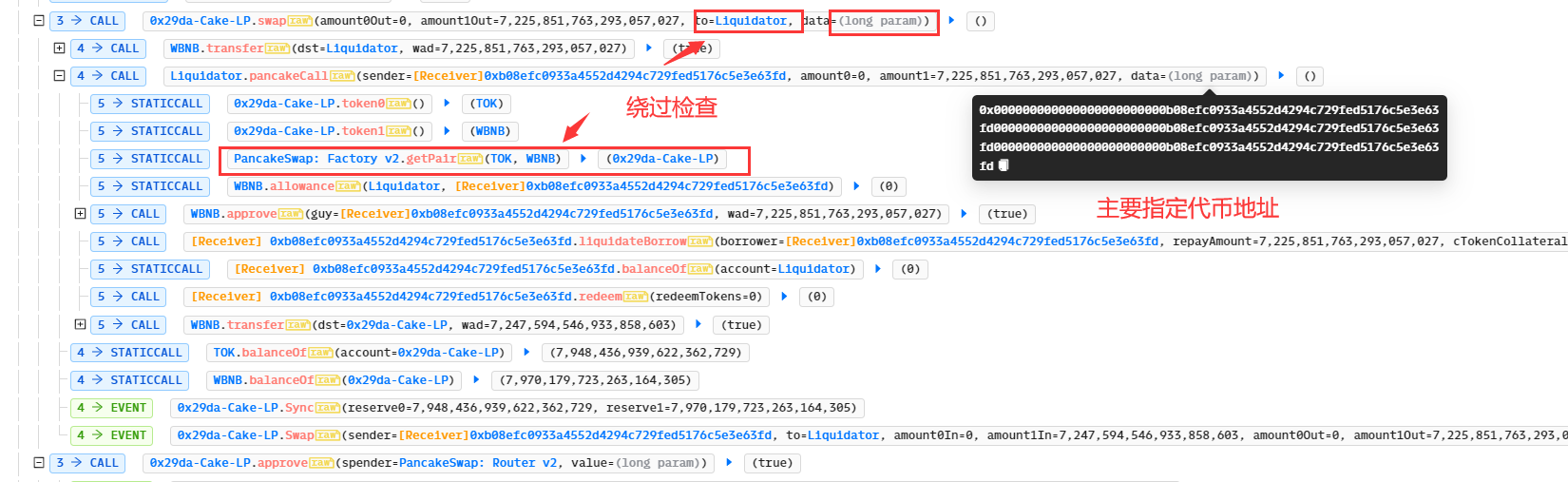
- 因为borrower、repayAToken、seizeAToken者三个地址均可被控制,从而实现了代币的转移控制:
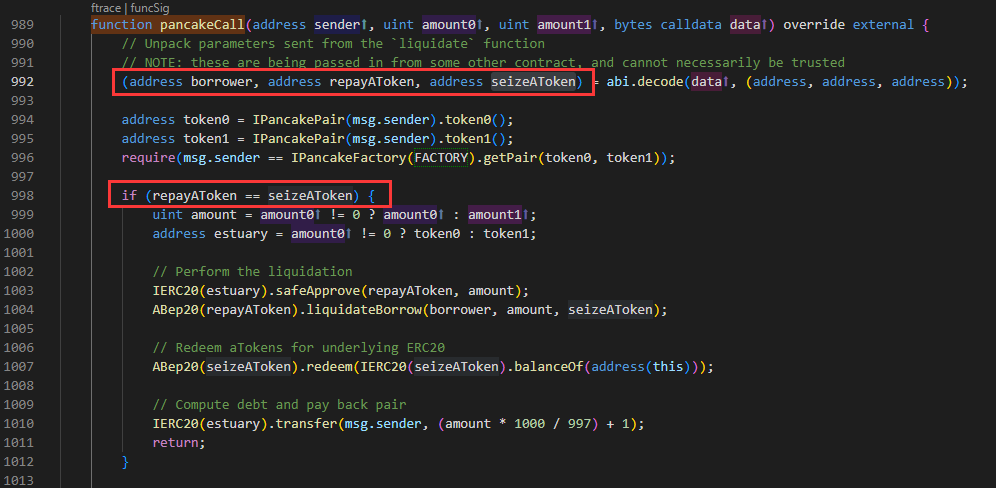
5. 其它类似的合约
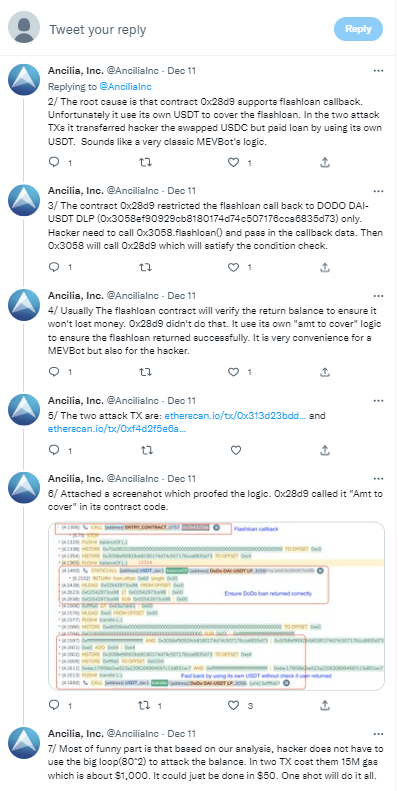
在其它的MEV合约的回调函数也存在同样的问题,具体细节可访问链接: https://twitter.com/AnciliaInc/status/1601778601702981633
- Uniswap V4 Hooks — Hooks介绍 — 找到你的问题的答案 359 浏览
- 为什么 MegaETH 是 DeFi Summer 2.0 的唯一机会 376 浏览
- Uniswap v4 架构与安全分析:Hooks、Singleton、Flash Accounting 432 浏览
- Hegotá 主题提案:EIP-8105 通用嵌入式加密内存池(EEM)- 魔术师 / 原始汤 239 浏览
- Hegotá头条提案:EIP-8105 通用嵌入式加密内存池 (EEM) - 魔术师 / 原始汤 314 浏览
- Hegotá 主题提案:EIP-8105 通用加密内存池(EEM)- 魔术师 / 原始汤 268 浏览

